The Code: Explained
Running from 2 November to 12 December 2011 our innovative challenge was designed to engage with people who are interested in code breaking and ethical hacking, and who may not have heard of GCHQ job opportunities via our traditional recruitment advertising and campaigns.
The Problem:
The Code Explained
The three stages within the challenge are designed so that participants can demonstrate the basics of analysing shellcode and obfuscation mechanisms, reverse engineering of malicious binary code and vulnerability analysis. These techniques are fundamental skills for a cyber security specialist at GCHQ.
Stage 1
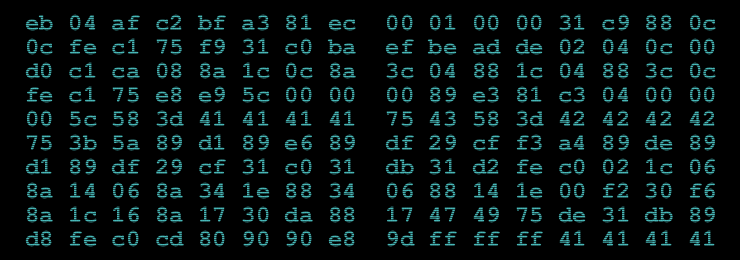
This starts with the main image on the canyoucrackit.co.uk site. To solve this stage it is necessary to identify that this is code that can be run by an Intel x86 compatible processor. After analysis, it is clear that this machine code implements the RC4 decryption algorithm, and is able to decrypt a block of data that is hidden inside the PNG file, in a comment tag. Once decrypted, this data reveals the location of stage 2 of the challenge.
Stage 2
This is a JavaScript programming challenge, with a cyber security angle. To solve this stage an implementation of a simple virtual processor is required. Some notes on the architecture are provided along with a block of data that can be analysed. Solving this stage will reveal the final stage of the challenge.
Stage 3
The final stage is a reverse engineering challenge. An executable file can be downloaded from the location revealed in stage 2. This executable parses a licence file - if it gets given a correct input, the challenge is revealed to be over, and a link to the 'success' page is provided to the participant.
We included a number of ways that this stage could be solved, as we are interested to see how people would attack the problem - coming up with innovative solutions to seemingly impossible problems is the day job at GCHQ. For example, there has been some comment by security experts on the fscanf buffer overflow that we included in this executable - one option to solving the problem would be to use this overflow to skip over certain checks in the executable. Other alternatives for this stage involved breaking the weak crypt, patching the executable directly to bypass the check, or analysing the assembly instructions and realising that this was all a complete diversion.
The three stages of this challenge highlighted a number of different machine code analysis techniques -
why does GCHQ care about these techniques (and indeed other types of machine code analysis)?
GCHQ cyber security specialists spend time analysing executable code from many sources. Sometimes it can be from malware that has been discovered, to work out what it does, and where it comes from. On other occasions it can be to assist in the assessment of a security product, to ensure that what the developer has intended to do is actually what they've achieved in practice.
Obviously, searching online for a solution - or even the completion page - is the simplest way to solve each of the stages of the challenge (various hints, links and partial solutions have been placed online since the challenge began), but we are really pleased to see how many people have independently tackled this challenge and shown the depth and breadth of skills which exist in this community.
This recruitment challenge was devised by our technical staff to exercise the critical skills which are needed to help defend UK networks from cyber attack: "Designing this challenge took us away from our day jobs for a very small amount of time and yet gave us the opportunity to engineer something that was both fun and technically intricate. Whilst being very similar to the work we do on a daily basis, it was incredibly rewarding to follow the external attention and analysis that the challenge generated."
The campaign is now closed. However, if you enjoy applying these skills, and want to help safeguard national security, register your interest in our cyber roles via the button below.
